PRESENTED BY

Cyber AI Chronicle
By Simon Ganiere · 18th August 2024
Welcome back!
Project Overwatch is a cutting-edge newsletter at the intersection of cybersecurity, AI, technology, and resilience, designed to navigate the complexities of our rapidly evolving digital landscape. It delivers insightful analysis and actionable intelligence, empowering you to stay ahead in a world where staying informed is not just an option, but a necessity.
Table of Contents
What I learned this week
TL;DR
This week is the first article about Microsoft Copilot, from its basic architecture to its integration within Microsoft 365. Don't miss next week's edition, where I’ll discuss the essential security measures for Copilot » READ MORE
This week was another example of a huge data breach related to millions of Social Security numbers being leaked. Can only recommend the investigation from Krebsonsecurity.com. The background story on the company who leaked the data, National Public Data, is really interesting and worrying at the same time.
In other news the geopolitics continue to be a significant driver of cyber security activities. OpenAI confirmed they have disrupted a covert Iranian influence operation. I’m wondering how much of this aligned with the recent Microsoft report, where they mentioned, “[…] In total, we’ve seen nearly all actors seek to incorporate AI content in their operations, but more recently many actors have pivoted back to techniques that have proven effective in the past—simple digital manipulations, mischaracterization of content, and use of trusted labels or logos atop false information. […]” Interesting time and something to keep an eye on from understanding how threat actors are actually incorporating AI in their operations.
A busy Patch Tuesday from Microsoft, with six zero-days within a total of 85 CVEs. Here is a list of those 6 CVEs: CVE-2024-38213, CVE-2024-38193, CVE-2024-38189, CVE-2024-38178, CVE-2024-38107, CVE-2024-38106. If you have looked at those please prioritise, the one related to IPv6 (CVE-2024-38063) can be proven being nasty. You can find a full summary here and here. Obviously assess them within your own context to identify the ones that really matter for you.
Early August is also the time for Black Hat and Def Con 2024. Here is another pretty good summary of the key research and announcement from TechCrunch.
Check out as well some great report on Ransomware activities, which highlight that 6 ransomware groups are responsible for half of the ransomware attacks » READ MORE
The Project Overwatch community is growing. However there is still a majority of readers that don't subscribe. If the cybersecurity and AI content has helped you, subscribing would mean the world to me! The larger our community, the more we can share knowledge and experience to better manage cyber risks and adopt AI in a safe way.
What is Microsoft Copilot?
Microsoft Copilot aim to be a significant advancement in enterprise productivity tools, designed to integrate seamlessly into the Microsoft 365 suite. Positioned within the Microsoft ecosystem, it is embedded into the applications that are used on a daily basis by millions of employees such as Word, Excel, PowerPoint, and Teams. Copilot leverages advanced artificial intelligence to assist users in performing tasks more efficiently. By processing natural language prompts, Copilot generates intelligent suggestions, automates routine tasks, and provides contextual insights, all aimed at enhancing decision-making and collaboration across the organization.
The key differentiator for Copilot is that in addition to generate content, the fact that you can based those answers on the entire Microsoft ecosystem is a key advantage. By utilizing data from the Microsoft Graph—encompassing emails, documents, and other organizational content—Copilot ensures that its outputs are tailored to the specific context of each user’s work. This capability positions Copilot as a strategic tool for enterprises, enabling them to harness AI-driven insights while maintaining the familiar workflows of Microsoft 365.
Technical Foundations
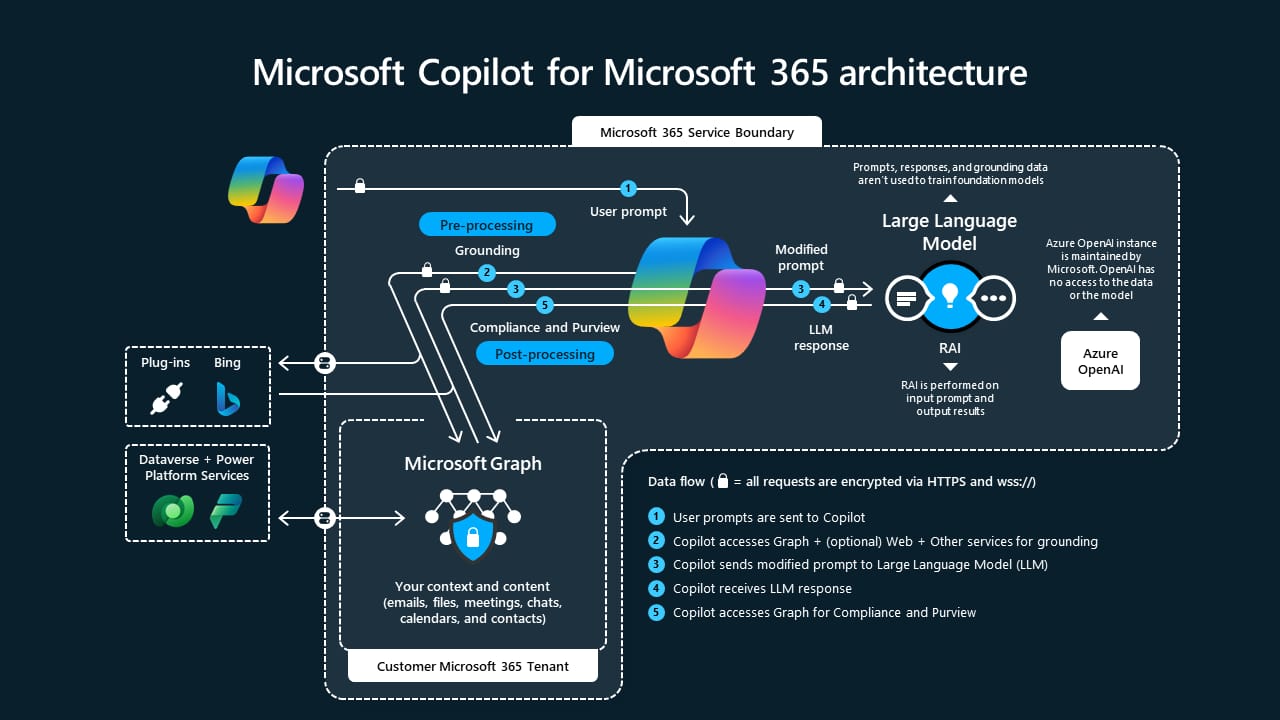
The architecture of Copilot for Microsoft 365 is described in the above diagram. Below is a high level summary of the key components.
Microsoft Graph: Microsoft Graph is the API framework that connects and manages data across the Microsoft 365 ecosystem, including emails, files, chats, and more. It provides real-time access to this data, ensuring Copilot can retrieve relevant information based on user permissions and context.
Large Language Models (LLMs): LLMs, such as those based on GPT-4, power Copilot's ability to understand and generate human-like text. These models interpret user prompts and generate responses by processing vast amounts of data, enabling Copilot to assist with tasks like drafting documents or summarizing information.
Semantic Index: The Semantic Index enhances data retrieval by understanding the relationships between different pieces of content. It enables Copilot to deliver more accurate and contextually relevant responses by going beyond simple keyword searches.
Grounding Process: Grounding refines user prompts by querying Microsoft Graph for relevant context before they are processed by the LLMs. This ensures that the responses generated by Copilot are specific and actionable.
Post-Processing and Orchestration Engine: After generating a response, Copilot uses post-processing to ensure the output is secure, compliant, and relevant. The orchestration engine manages these steps, integrating the response seamlessly into Microsoft 365 applications.
Plugins and Extensibility: Plugins extend Copilot’s functionality by integrating with third-party tools and services. These allow Copilot to perform specialized tasks and access additional data sources, all while maintaining security and compliance within the Microsoft 365 environment.
What Values Does This Bring to Enterprise?
Microsoft Copilot is deeply integrated into the Microsoft 365 ecosystem. This integration allows users to access Copilot’s features directly within these apps, making it a seamless part of their workflow.
Role of Microsoft Graph: The Microsoft Graph is central to Copilot’s functionality, connecting it to data across the Microsoft 365 suite. By accessing emails, documents, chats, and meetings through the Graph, Copilot can provide contextually relevant information while adhering to existing security and permission settings.
Cross-Application Support: Copilot’s ability to function across multiple applications ensures users can retrieve relevant information no matter which Microsoft 365 tool they are using. For example, in Teams, Copilot can summarize a discussion by referencing data from Outlook or SharePoint, providing comprehensive support in real-time.
Enterprise Control: Administrators can manage Copilot through Microsoft 365’s existing tools, ensuring it complies with organizational security policies. Additionally, Copilot’s functionality can be extended through plugins, integrating it with other systems within the enterprise.
What About Security?
As with any technology that interacts with sensitive data, understanding and addressing security implications is critical. In the next article, we will dive into the security aspects of Microsoft Copilot, including how it handles data privacy, what safeguards are in place to protect organizational information, and how a thorough threat model analysis can help mitigate potential risks. Ensuring that Copilot operates within a secure and compliant framework will be essential for organizations looking to fully leverage its capabilities while maintaining robust data protection standards.
Sources
Worth a full read
Ransomware Review: First Half of 2024
Key Takeaway
Six ransomware groups are responsible for over half of all compromises in 2024.
Newly disclosed vulnerabilities are the primary drivers of ransomware activity.
Law enforcement operations significantly disrupt ransomware group activities.
The U.S. accounts for over half of the global ransomware attacks in 2024.
Manufacturing and healthcare sectors remain prime targets for ransomware attacks.
Law enforcement actions are extending to organizations affiliated with ransomware groups.
Ransomware groups frequently misrepresent data sources on leak sites.
Ransomware groups use double-extortion tactics, leaking stolen data if ransoms are unpaid.
Ransomware groups are evolving and rebranding to avoid law enforcement scrutiny.
The success of ransomware has led to a growing pool of threat actors seeking fame and fortune.
1762 new posts on ransomware leak sites in the first half of 2024.
Six ransomware groups accounted for more than half of the compromises observed.
Manufacturing, healthcare, and construction were the industries most impacted by ransomware.
The U.S. accounted for 52% of total ransomware attacks in the first half of 2024.
Using AI for Offensive Security
Key Takeaway
AI augments offensive security by automating tasks and enhancing human capabilities, improving efficiency.
Human oversight is vital for validating AI outputs, ensuring accuracy and maintaining a technical edge.
AI agents' cyclic approach enables continuous learning and adaptation, enhancing complex problem-solving.
Balancing AI automation with human oversight prevents unintended consequences in offensive security.
AI lowers barriers to entry, democratizing security testing and allowing broader participation.
AI's integration into offensive security requires robust GRC frameworks to ensure ethical, secure use.
AI-powered tools process vast data, uncovering patterns unrecognizable to humans, aiding vulnerability discovery.
AI enhances professional security testers' productivity, focusing on strategic and complex tasks.
AI can autonomously exploit vulnerabilities, including zero-day exploits, with high success rates.
Offensive security must evolve with AI capabilities, fostering a culture of responsible AI use.
Some more reading
Ransomware Tool Matrix » READ
OpenAI announced structured outputs, where model outputs now reliably adhere to developer-supplied JSON Schemas. » READ
Law firms hit with average ransom demand of $2.5 million. Since 2018 138 legal firms across the globe have publicly confirmed ransomware attacks on their system impacting at least 2.9 million records. » READ
Walmart is using generative AI to create and improve over 850 millions pieces of data in their catalog » READ
Wisdom of the week
Strong leaders
are long on visions.
Weak leaders
are short on sight.
Contact
Let me know if you have any feedback or any topics you want me to cover. You can ping me on LinkedIn or on Twitter/X. I’ll do my best to reply promptly!
Thanks! see you next week! Simon